Kubernetes Security Landscape in 2024: A Look at the Top Concerns
The Red Hat State of Kubernetes Security report for 2024 offers a comprehensive analysis of the evolving security landscape in the Kubernetes ecosystem. While the report highlights several improvements in Kubernetes security practices, it also reveals persistent challenges and emerging trends that require attention.
Misconfigurations Remain a Top Security Concern
Despite a decrease in the number of misconfigurations reported, they still pose a significant threat to Kubernetes security. The report indicates that misconfigurations continue to be a leading cause of security vulnerabilities, particularly in deployments with complex configurations. This emphasizes the importance of meticulous configuration management and the use of automated tools to detect and rectify misconfigurations.
The Rise of Vulnerabilities and the Need for DevSecOps
The report also underscores the growing concern about vulnerabilities. The increasing complexity of Kubernetes deployments, coupled with the rapid pace of software development, creates a fertile ground for vulnerabilities. This trend emphasizes the need for robust vulnerability management practices, including continuous security scanning and the adoption of DevSecOps methodologies.
DevSecOps: Bridging the Gap Between Development and Security
DevSecOps practices play a crucial role in mitigating security risks. By integrating security considerations into every stage of the development lifecycle, DevSecOps helps to identify and address vulnerabilities early, reducing the potential for security breaches. This collaborative approach fosters a culture of shared responsibility between development and security teams, improving the overall security posture of Kubernetes deployments.
The Importance of Continuous Security Scanning
Continuous security scanning is another key component of a robust security strategy. By regularly scanning Kubernetes environments for vulnerabilities, organizations can identify and remediate potential risks promptly. Automated security scanning tools can greatly simplify this process, enabling organizations to stay ahead of emerging threats and ensure ongoing security compliance.
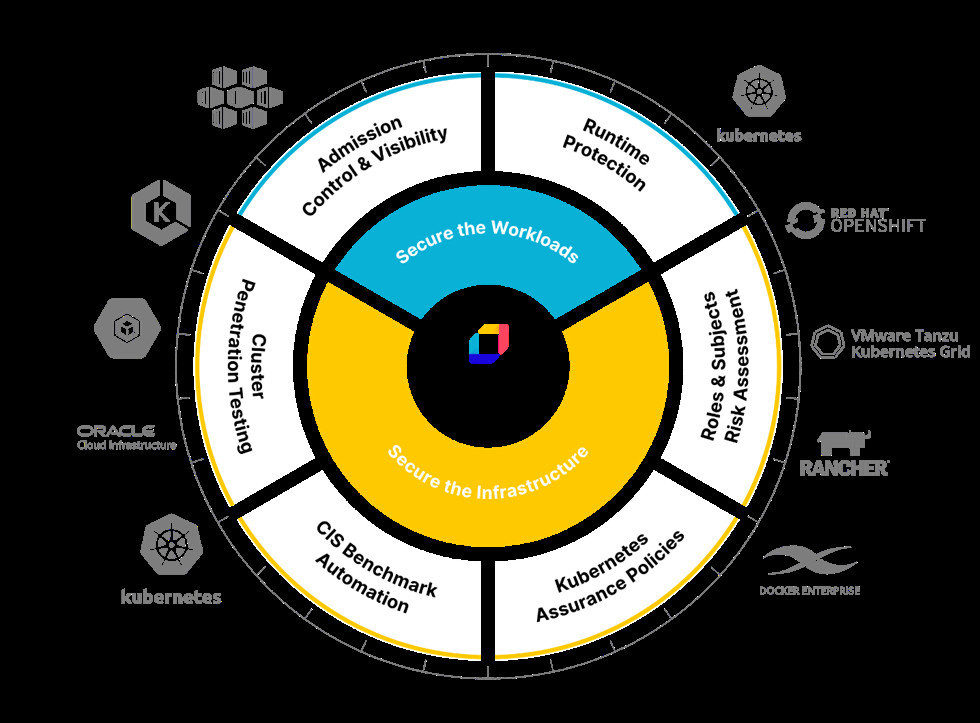
ARMO: A Holistic Approach to Kubernetes Security
ARMO Platform offers a comprehensive solution for securing Kubernetes environments. Its platform addresses all the key security concerns highlighted in the Red Hat report, including misconfigurations, vulnerabilities, and real-time attacks.
ARMO's Unique Approach: Leveraging eBPF Technology
ARMO Platform leverages the power of eBPF technology to provide deep runtime visibility and comprehensive security coverage. Its eBPF-based sensor captures detailed runtime information about infrastructure and application behavior, enabling real-time threat detection and response.
A Virtuous Cycle of Security
ARMO's eBPF-powered platform creates a virtuous cycle of security by:
-
Identifying security gaps and risks during runtime: ARMO's posture management capabilities identify potential vulnerabilities and misconfigurations at runtime, enabling proactive remediation.
-
Signaling emerging high-priority attack paths: ARMO's runtime analysis provides context for vulnerability management, enabling organizations to prioritize remediation efforts based on the most critical risks.
-
Supporting hardening measures without compromising application uptime: ARMO helps organizations implement security hardening measures without impacting application performance or availability.
-
Ensuring continuous compliance: ARMO's continuous monitoring and enforcement capabilities help organizations maintain compliance with industry standards and regulations.
Conclusion: Embracing a Proactive Security Posture for Kubernetes
The 2024 Red Hat State of Kubernetes Security report serves as a valuable resource for organizations seeking to enhance their Kubernetes security posture. The report highlights the importance of proactive security measures, including continuous scanning, DevSecOps adoption, and the use of comprehensive security solutions like ARMO Platform. By embracing a holistic and proactive approach to security, organizations can effectively mitigate risks and safeguard their critical applications within the dynamic Kubernetes environment.
Moving Forward: Staying Ahead of the Curve in Kubernetes Security
As Kubernetes continues to evolve and gain widespread adoption, the need for robust security measures will only intensify. Organizations must stay informed about the latest threats and vulnerabilities, leverage innovative technologies like eBPF, and embrace a collaborative approach to security through DevSecOps. By adopting these best practices, organizations can ensure the security and resilience of their Kubernetes deployments, enabling them to realize the full potential of this transformative technology.